Decoupling Drupal 8 core: Retrieving and manipulating content with core REST
April 26, 2018Reprinted from the Acquia Developer Center with permission from DC Denison (Senior Editor, Acquia).
As we saw in a previous installment of Experience Express, because Drupal has a HAL-compliant REST API available out of the box with minimal configuration, you can easily provision an API that can immediately be employed to consume content entities and manipulate them from other applications. Now that we have successfully exposed content entities as REST resources, used Entity Access to govern permissions, and customized the formats and authentication mechanisms in use by the core REST API, it is now time to move into actually retrieving and manipulating that data.
Luckily, if you are familiar with other REST APIs, issuing HTTP requests against Drupal core to obtain the data you require in your application is simple. In this column, we will inspect the key components of most requests to the core REST API, how to retrieve and update content entities via core REST, and how to create and delete them.
Issuing REST requests against Drupal core
Because REST is an architectural pattern that operates on HTTP, it makes use of HTTP verbs, which can be categorized into safe and unsafe methods. Often, however, this does not provide enough protection, so Drupal has provided an additional mechanism — the X-CSRF-Token request header — to ensure that unsafe methods cannot be used nefariously. Finally, because Drupal flexibly serves responses across a variety of serialization formats, a query argument must be provided that contains the appropriate serialization format.
Safe and unsafe methods
In HTTP, verbs — also known as request methods — include
GETHEADPOSTPUTDELETETRACEOPTIONSCONNECTPATCHHEADGETOPTIONSTRACEAmong the methods listed above, we will only be considering
GETPOSTDELETEPATCHGETPOSTDELETEPATCHWhile
PUTPUTGETThere are other Drupal-specific motivations for the lack of
PUTPUTPATCHThe X-CSRF-Token
request header
X-CSRF-TokenCross-site request forgery (CSRF) is a scenario in which a consumer application with permissions to manipulate data behind the API could issue malicious requests against the API, even without the consumer application's knowledge. This is because the consumer application may not necessarily have the protections required to filter out potentially harmful data contained therein, particularly if the request contains user-generated data.
In order to protect itself from CSRF attacks, Drupal 8 obligates all requests to define an
X-CSRF-TokenPOSTPATCHDELETE/session/tokenX-CSRF-TokenSpecifying serialization formats
Because Drupal can flexibly handle multiple serialization formats, including HAL+JSON, JSON, and XML, all requests to the core REST API must include a query argument specifying the serialization format used in the request. This is the case even if only one serialization format is configured to be supported in the core REST API (such as JSON).
When issuing requests against Drupal's core REST API, you must append to each URI the query argument
?_formatGETcore-rest.dd:8083/node/1?_format=hal_jsonWhen a request body contains data in a particular serialization format, which is the case of unsafe methods such as
POSTPATCHContent-TypeNote: While
AcceptAcceptRetrieving content entities with core REST
If you do not currently have a test site like the one we set up previously, return to that previous installment of Experience Express to set up a site like
core-rest.dd:8083GETGETgranularity: resource
configuration:
methods:
- GET
formats:
- hal_json
authentication:
- basic_authIn Postman, you can issue a
GET/node/1?_format=hal_json/node/1?_format=hal_json200 OK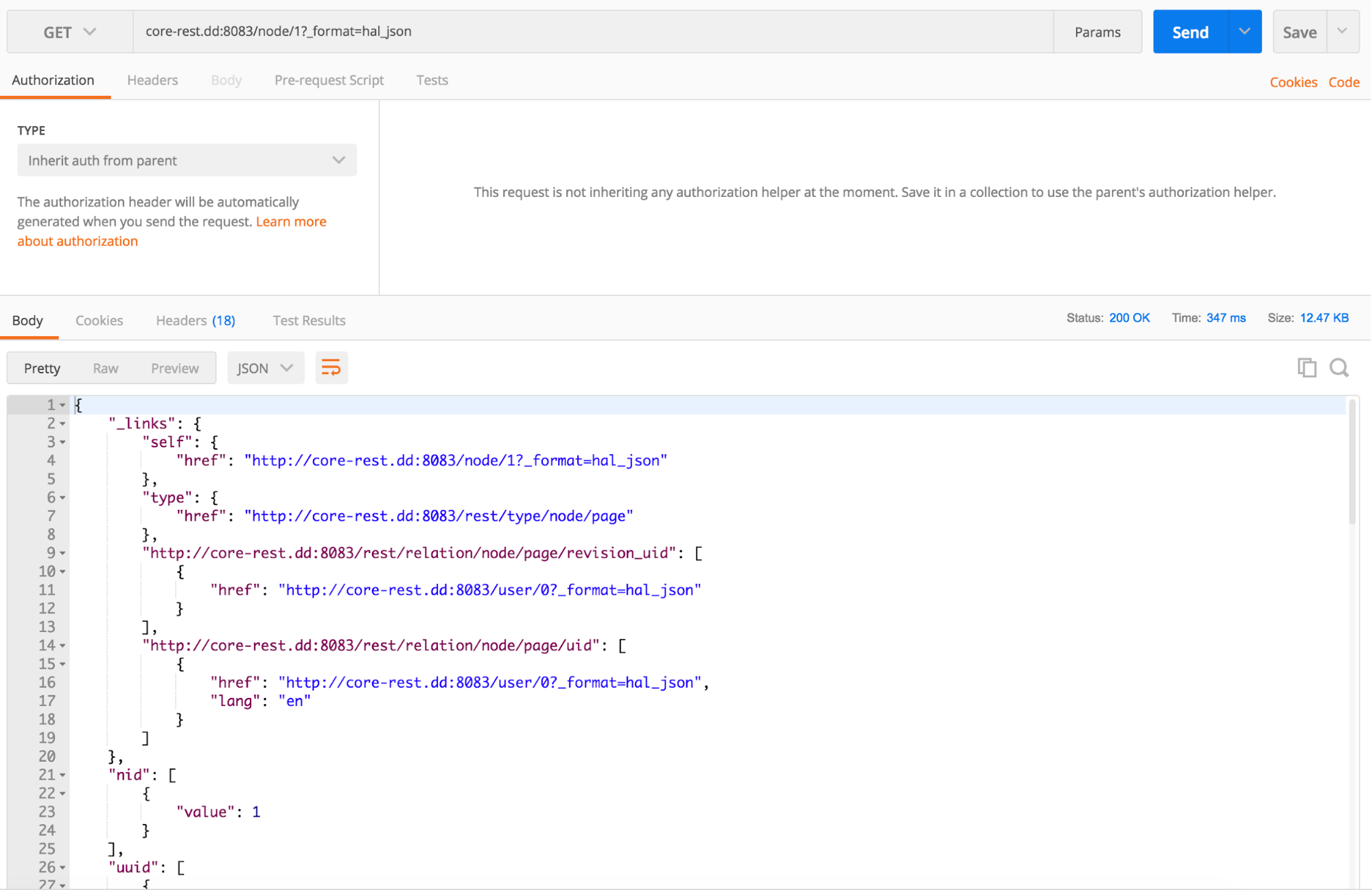
Creating content entities with core REST
Issuing successful
POSTgranularity: resource
configuration:
methods:
- POST
formats:
- hal_json
authentication:
- basic_authBefore issuing our request, we must first craft our request body to include the data structure we want Drupal to use to create our new content entity. In order to do this with HAL+JSON, we will also need to include the correct
_links_linksGETImportantly, the request payload should never include a UUID, as that is assigned by Drupal when the content entity is created.
POSTX-CSRF-TokenGET/rest/session/tokenEh1INrGyEUNBog5ZL2o-dHFPnLoseIKCcL35aVSGg94X-CSRF-Token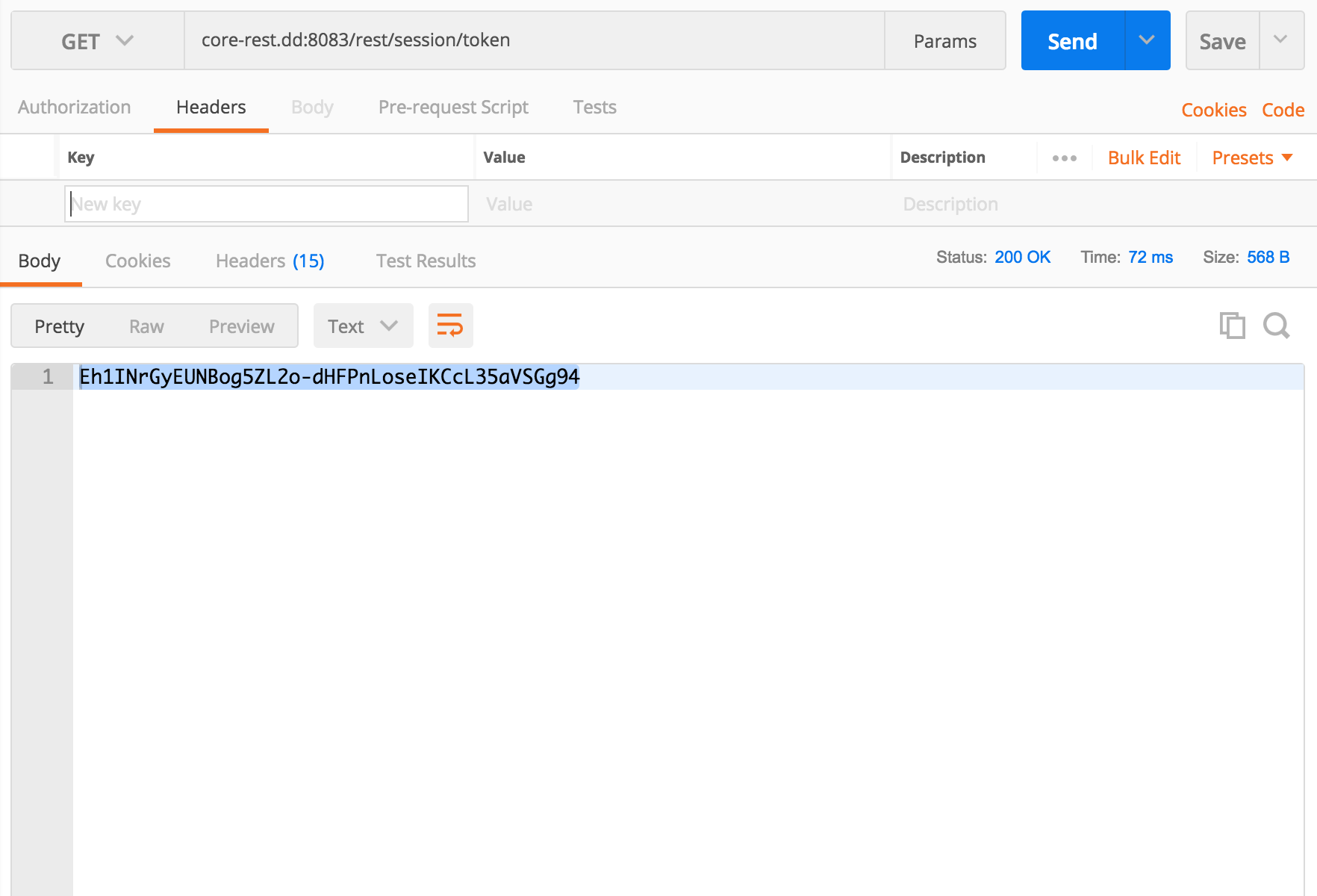
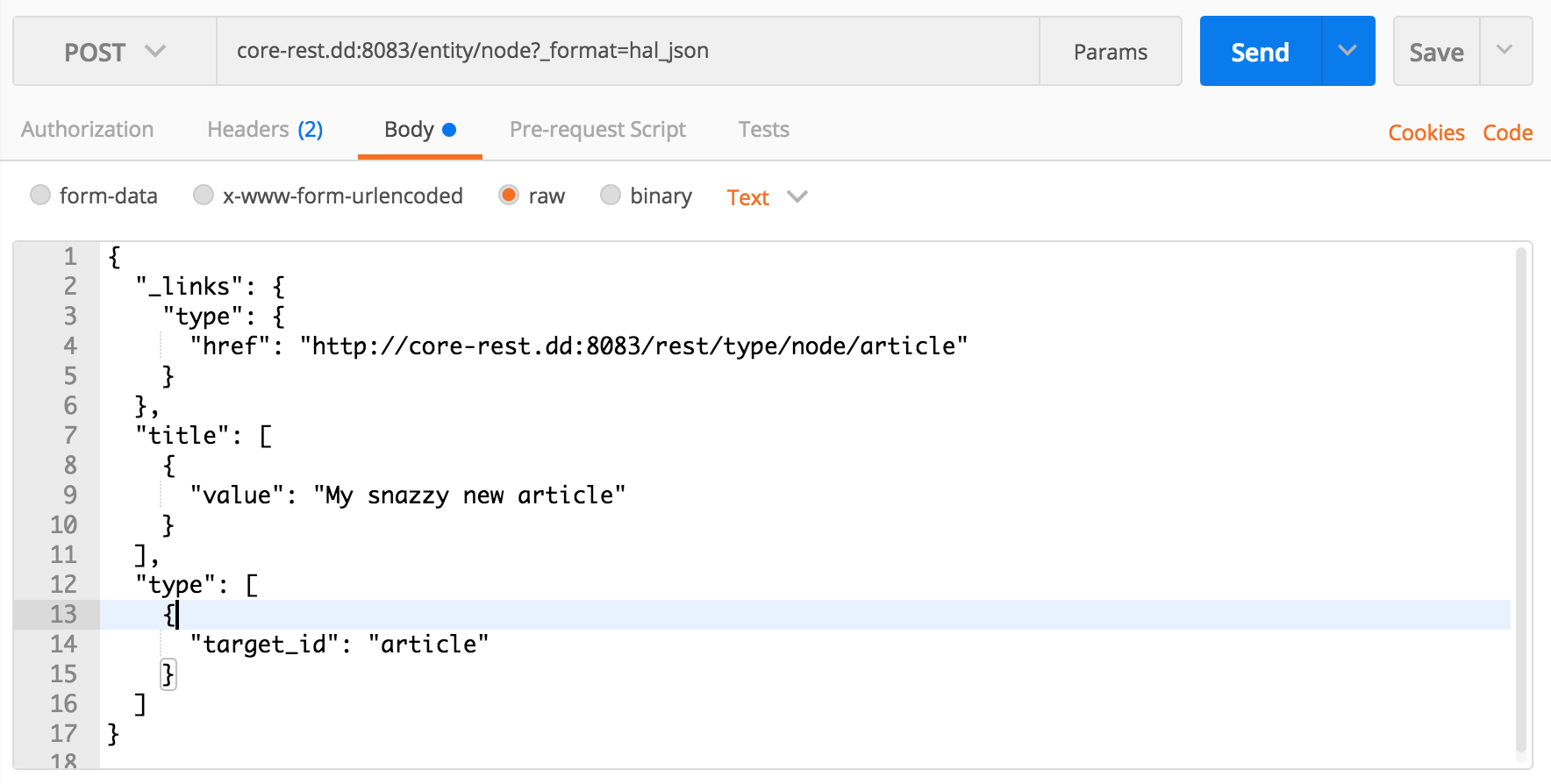
To create a new article, for instance, we can craft a
POST{
"_links": {
"type": {
"href": "http://core-rest.dd:8083/rest/type/node/article"
}
},
"title": [
{
"value": "My snazzy new article"
}
],
"type": [
{
"target_id": "article"
}
]
}
At this point, because we are primarily focused on how to form a request, we will make our lives easier by not using any built-in authentication, which will be covered in a future installment. This is extremely dangerous and highly inadvisable live on production, but we can do this safely on a local production environment. While user-generated content is an exception, operations across the API by applications are typically riskier because it isn't possible for Drupal to control how or how much of that content is introduced.
For the purposes of this blog post, we'll enable an anonymous user to create content by navigating to People > Permissions in Drupal's administration toolbar. Grant the following permissions to the Anonymous user role on the appropriate content types (currently we are only working with Articles and Basic pages): Create new content (i.e.
POSTDELETEPATCHThen, back in Postman, in the request headers, we will want to provide the
X-CSRF-TokenGETX-CSRF-Token: Eh1INrGyEUNBog5ZL2o-dHFPnLoseIKCcL35aVSGg94Content-TypeContent-Type: application/hal+json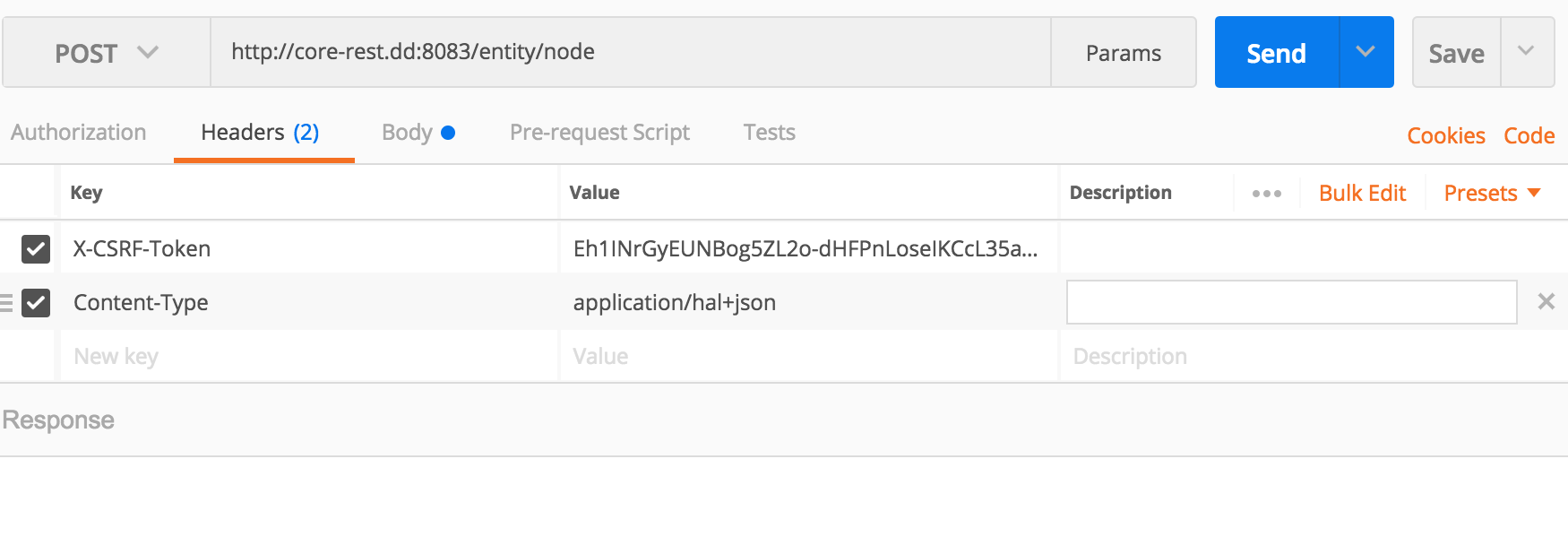
In Postman, you can issue a
GET/node/1?_format=hal_json/node/1?_format=hal_json200 OKNow, in Postman, we can issue a
POST/entity/node?_format=hal_json201 CreatedHere is what we're given by Postman:
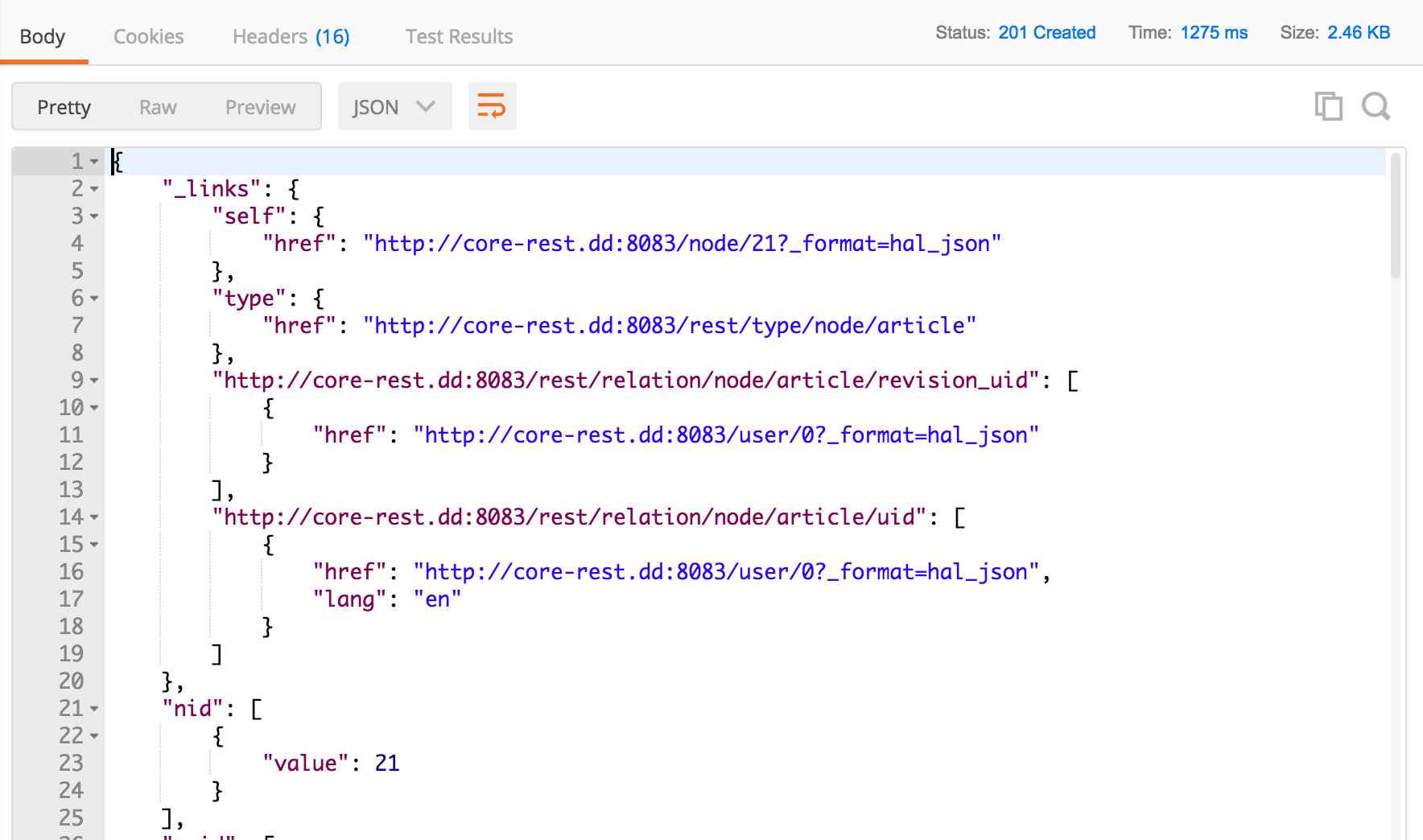
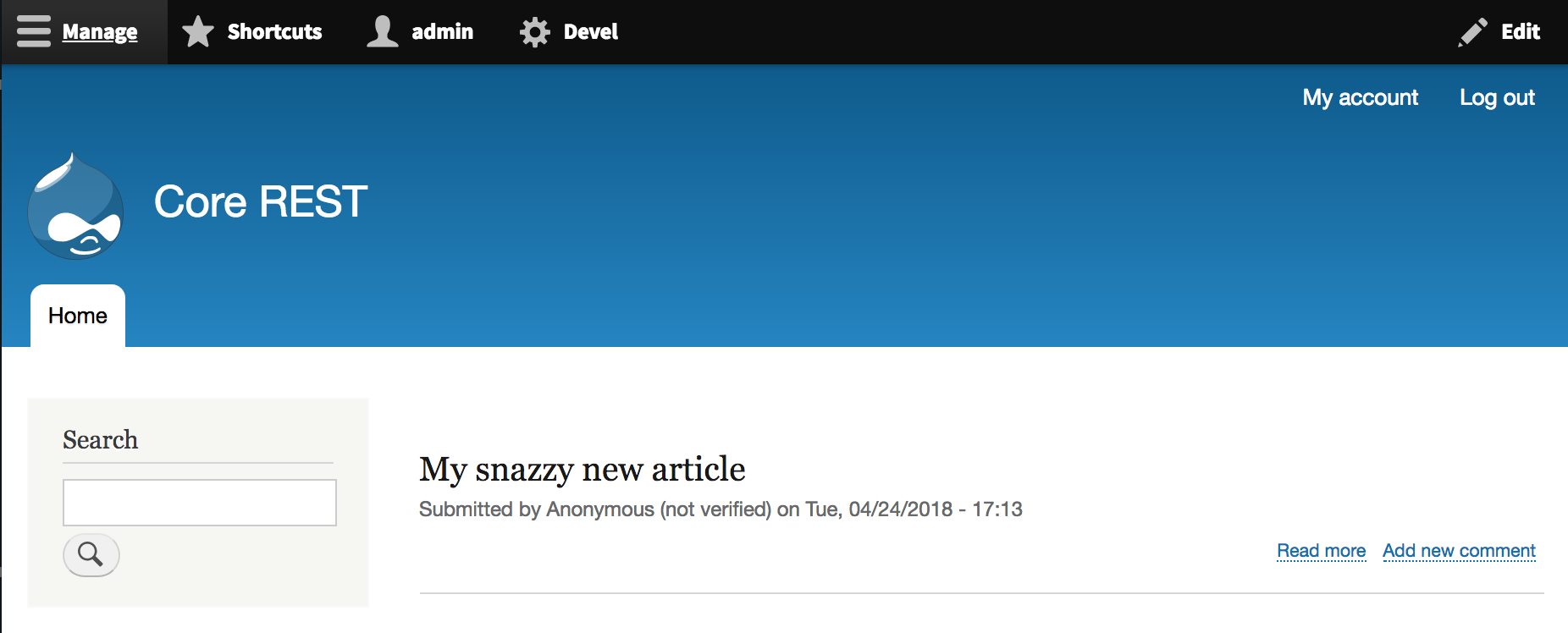
If we navigate to our home page, which currently displays content ordered by most to least recent, we can see our new article has been created by Anonymous. Because we did not provide anything in the body field, the article only has a title.
Note: As of Drupal 8.3.0, it is possible to issue requests against the resource
/node/entity/nodeUpdating content entities with core REST
Now that we've created our snazzy new article, how do we update it in cases where our marketing team needs the title to change or our client would like slightly adjusted text? Issuing successful
PATCHgranularity: resource
configuration:
methods:
- PATCH
formats:
- hal_json
authentication:
- basic_authAs we saw with
POST_linksPATCHPOSTPATCH403 ForbiddenOn the other side of the spectrum, there are certain components of a
PATCHNote: Since Drupal 8.1.0, all successful
PATCH200 OK204 No ContentTo begin, we need to craft a
PATCHX-CSRF-Tokeni7GUIxfEYRR3nzcNyremz9Q73sdyTpStSoCsU7J0NQw_links{
"_links": {
"type": {
"href": "http://core-rest.dd:8083/rest/type/node/article"
}
},
"title": [
{
"value": "My snazzy and snappy new article"
}
],
"type": [
{
"target_id": "article"
}
]
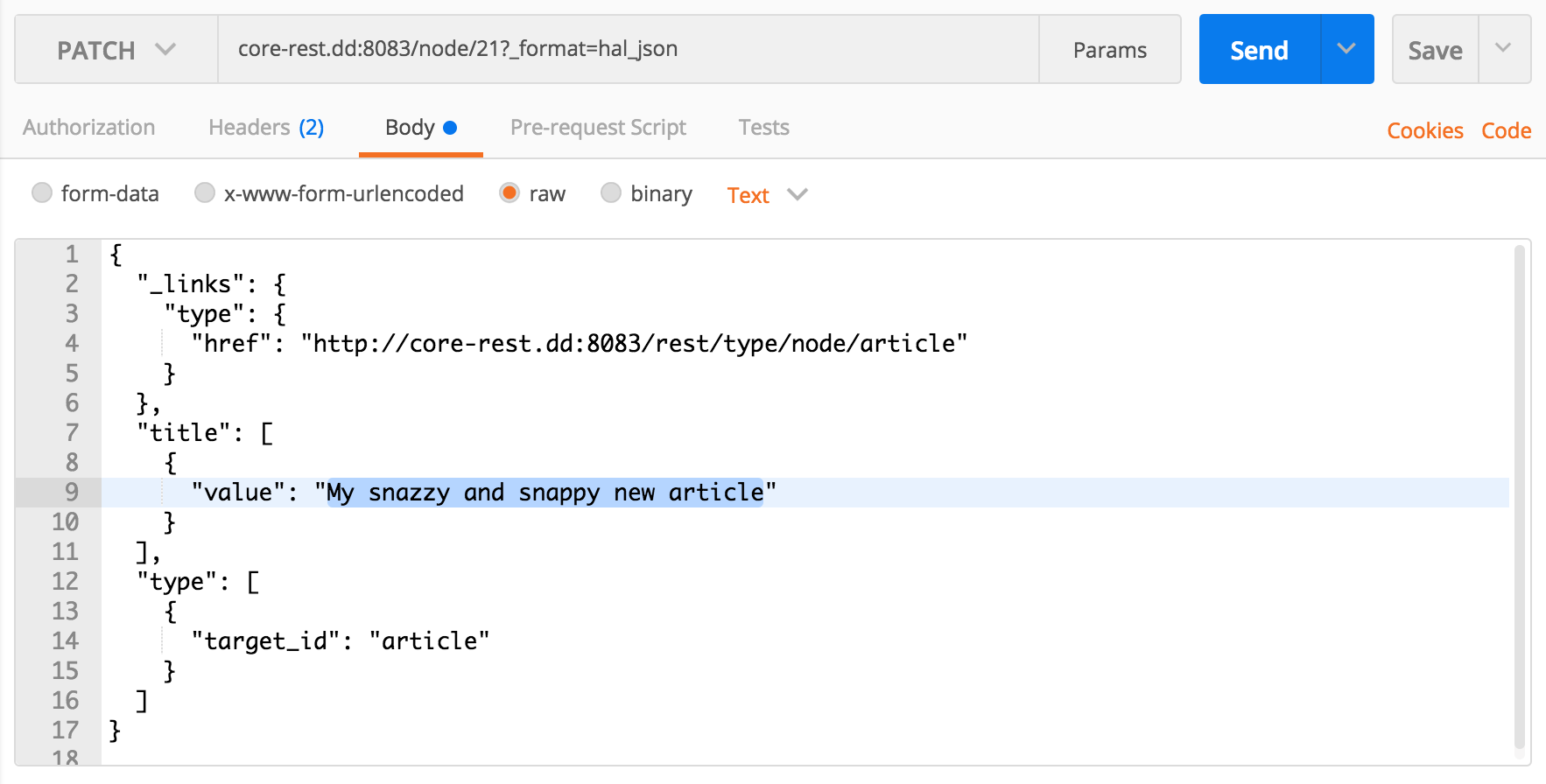
}In this case, because we are only changing the title field (our title is changing to "My snazzy and snappy new article"), we don't need to provide any other information about other fields. The
target_idHowever, because we are not creating a new entity, the resource we point the request to changes to the resource that we created in the previous section. This means that we need to acquire the identifier of the node (the nid) and target our
PATCH/node/21?_format=hal_jsonFirst, we provide the appropriate headers.
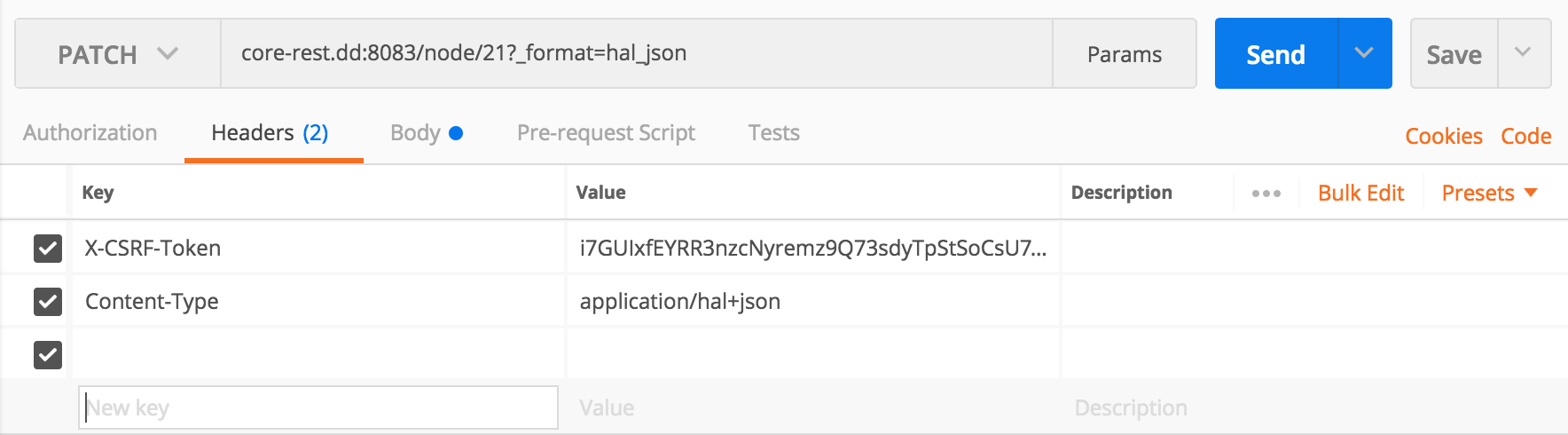
Then, we attach our changes in the request body.
Here is what we receive in return, a
200 OKPATCH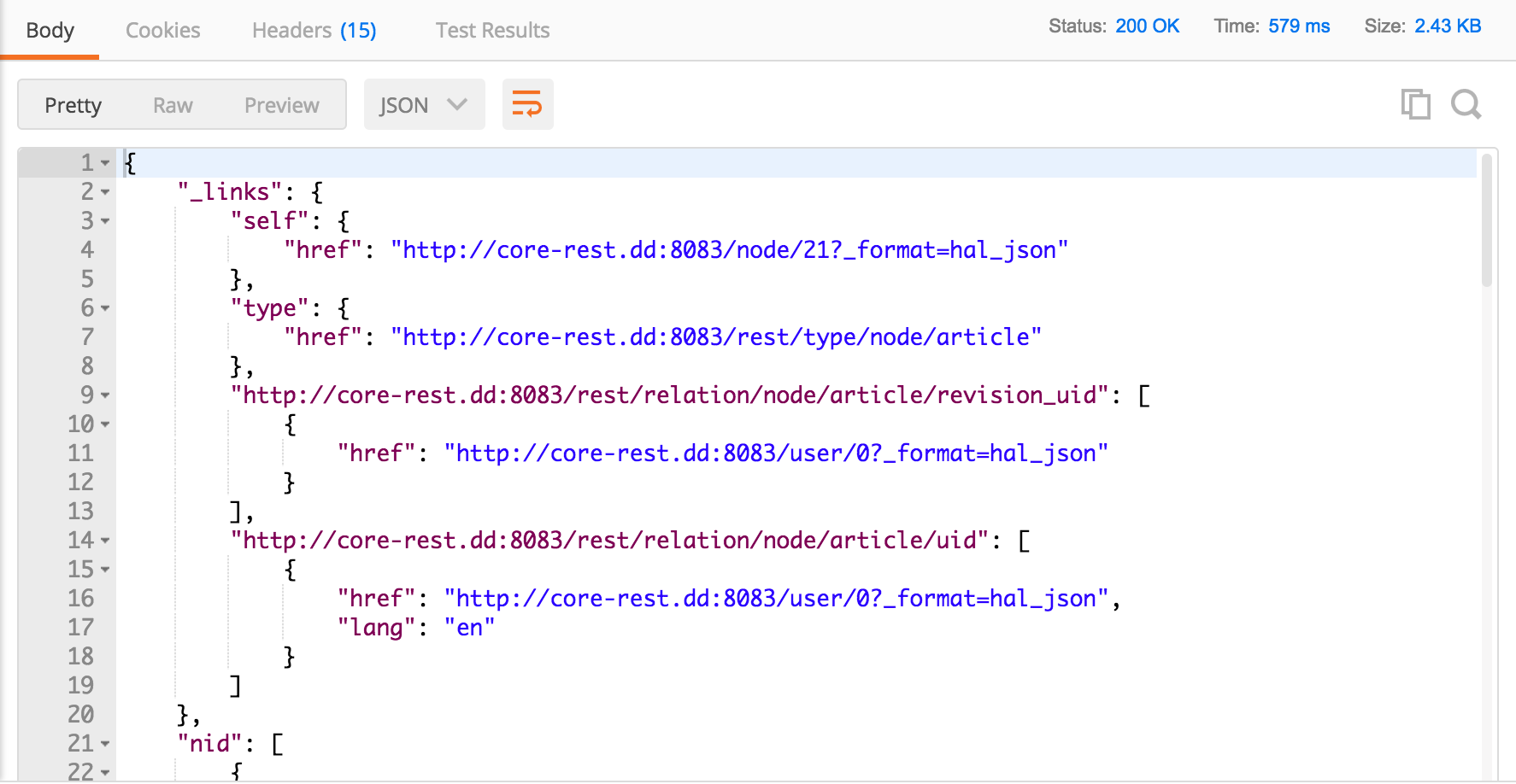
If we refresh the Drupal home page, we see that the article we created before has now been updated with our new title: pretty snazzy and snappy!
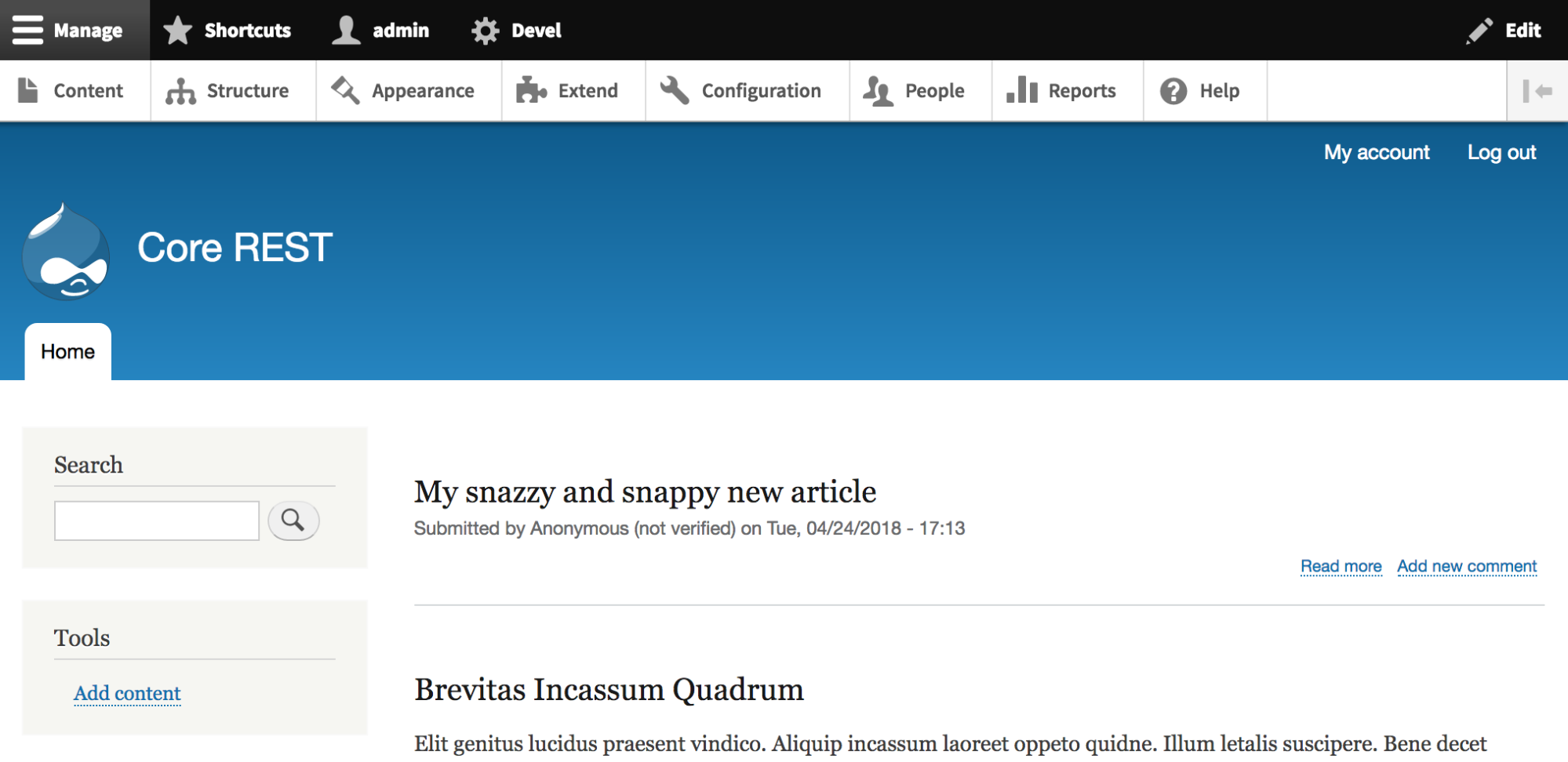
Deleting content entities with core REST
As it turns out, our customer is not a fan of the new article, despite its snazziness and snappiness. They've requested that we delete the article so that it does not appear in the consumer application. All content must go somewhere once it is no longer relevant or needed. For that, we need
DELETEDELETEgranularity: resource
configuration:
methods:
- DELETE
formats:
- hal_json
authentication:
- basic_authAfter retrieval of content with
GETDELETEContent-TypeAll we need to do is point our request at the resource in question with a suffixed query parameter —
/node/21?_format=hal_jsonDELETEX-CSRF-Token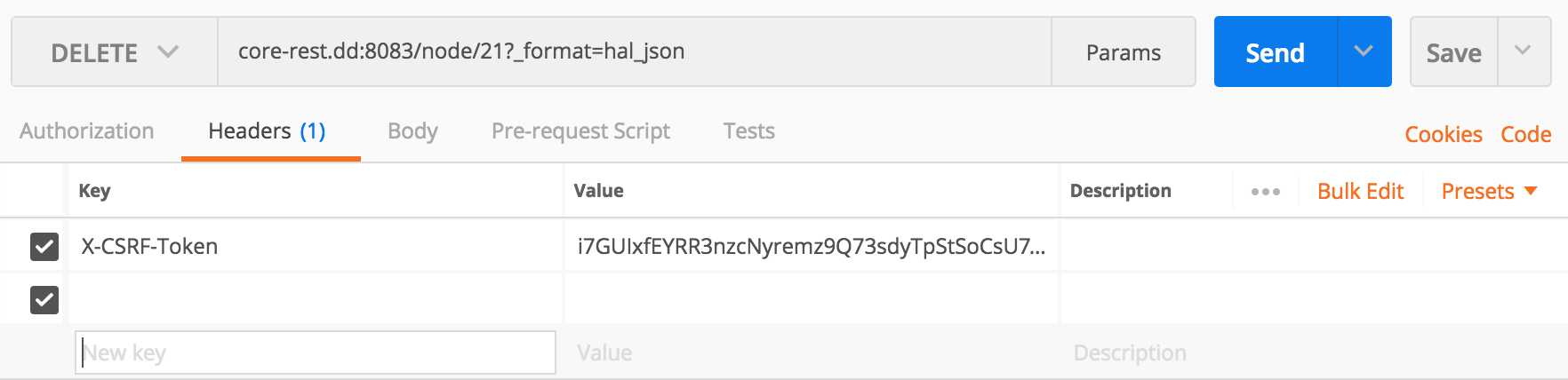
Here is what we receive in return, a
204 No Content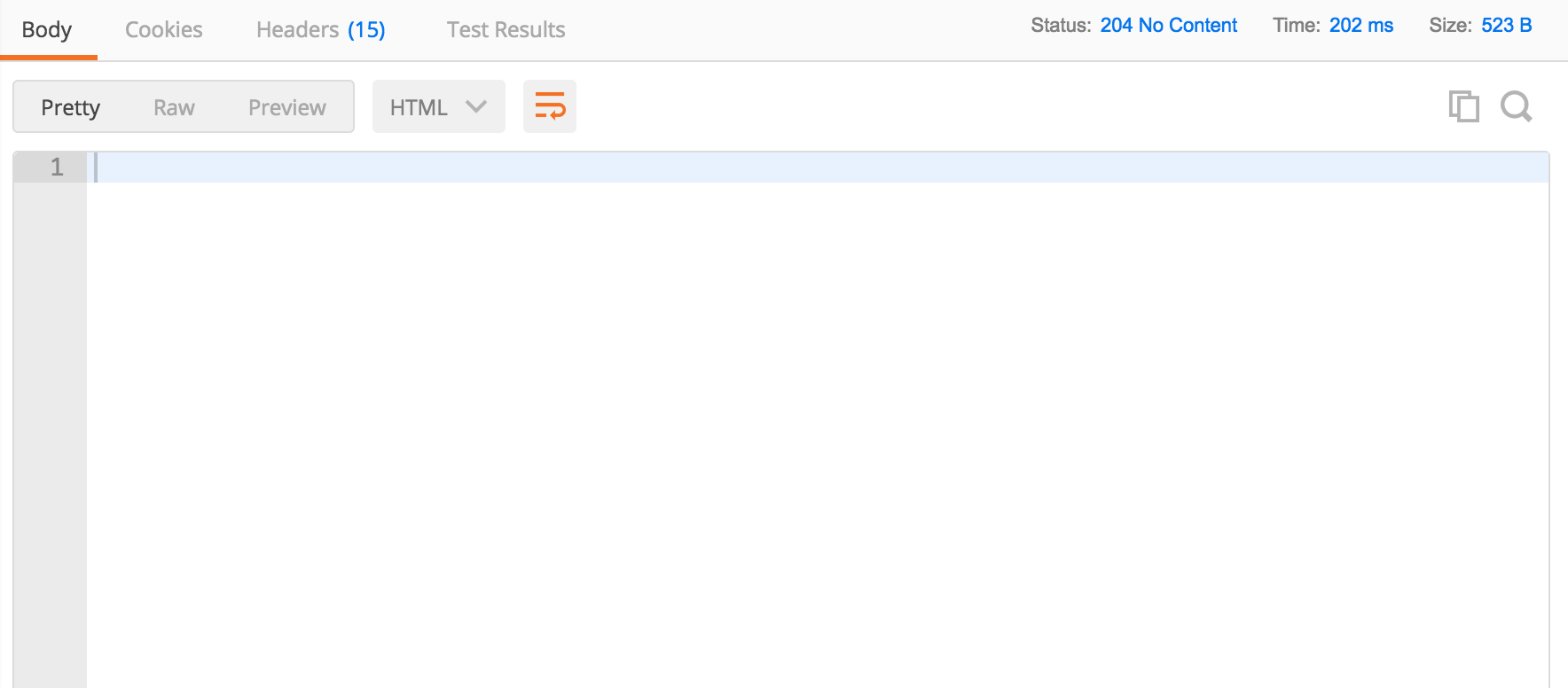
Sure enough, when we navigate to our Drupal home page again and refresh the page, we can see that the entity has now vanished! Success!
Conclusion
In this blog post, I introduced you to the key approaches in retrieving and manipulating content entities in Drupal through the core REST API employing simple use cases such as modifying a title or deleting an entity. As you can see, working with the core REST API is quite simple as long as you have configured permissions and REST resources correctly. While Drupal certainly is a unique case, and while these examples were trivial in order to demonstrate a consistent process to API testing that we will reuse later, the immediacy and directness of the core REST API are part of what make it so appealing.
Next time on the Experience Express, we're off to Philadelphia, where Drupaldelphia is part of the kickoff for Philly Tech Week. I'll be joining up with several others on a keynote panel about some of the exciting work happening around the future of Drupal 8 in response to the Driesnote at DrupalCon Nashville. You'll probably catch me having a roast pork sandwich (with sharp provolone and broccoli rabe, of course) at some point during the day!
Works cited
"Getting started: REST configuration & REST request fundamentals." Drupal.org. 17 May 2017. Accessed 2 April 2018.
Garfield, Larry. "Putting off PUT." Drupal.org. 26 February 2013. Accessed 2 April 2018.
Wehner, Daniel. "Accept header based routing got replaced by a query parameter." Drupal.org. 6 July 2015. Accessed 2 April 2018.
"POST for creating content entities." Drupal.org. 14 March 2018. Accessed 24 April 2018.
"PATCH for updating content entities." Drupal.org. 9 November 2016. Accessed 24 April 2018.
"DELETE for deleting content entities." Drupal.org. 11 July 2017. Accessed 24 April 2018.